Dailydave mailing list archives
Re: Dshell versus INNUENDO
From: "J. Craig" <3141592f () gmail com>
Date: Tue, 3 Feb 2015 14:31:46 -0800
Firstly, props to the dshell team for making that decoder and releasing it. Secondly, you shouldn't need a decoder to catch an implant using this type of channel. It's pretty high signal. Thx, Jason On Tue, Feb 3, 2015 at 11:06 AM, Dave Aitel <dave () immunityinc com> wrote:
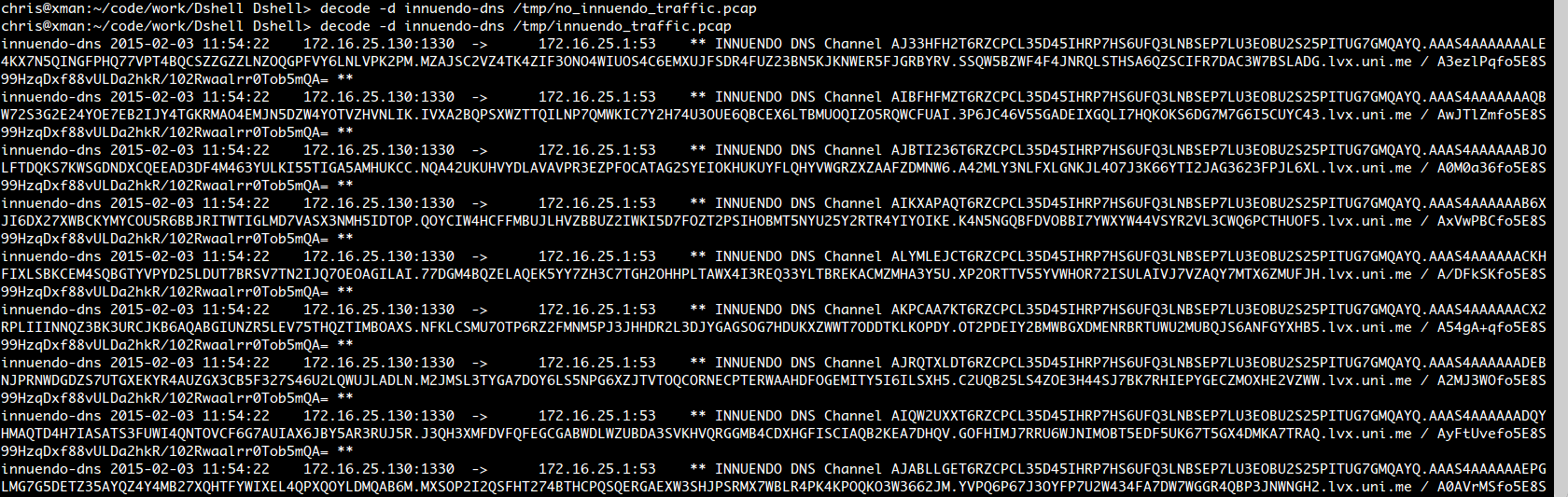
The US Army recently released DShell <http://gizmodo.com/the-army-just-open-sourced-its-security-software-1683023527>, which they've been using to do network incident response, as open source. Part of it is a DNS decoder <https://github.com/USArmyResearchLab/Dshell/blob/master/decoders/dns/innuendo-dns.py> that tries to find INNUENDO traffic. Although they developed it only by looking at our demonstration video <https://vimeo.com/115206626> (note: email admin () immunityinc com for an eval copy of INNUENDO!) we can confirm their script works (see below). It may, or may not, work against the *next* version of INNUENDO. ;> Thanks, Dave Aitel Immunity, Inc. [image: Dshell image] _______________________________________________ Dailydave mailing list Dailydave () lists immunityinc com https://lists.immunityinc.com/mailman/listinfo/dailydave
_______________________________________________ Dailydave mailing list Dailydave () lists immunityinc com https://lists.immunityinc.com/mailman/listinfo/dailydave
Current thread:
- Dshell versus INNUENDO Dave Aitel (Feb 03)
- Re: Dshell versus INNUENDO J. Craig (Feb 04)
- Re: Dshell versus INNUENDO Ben Creitz (Feb 04)
- Re: Dshell versus INNUENDO Dean Pierce (Feb 05)
- Re: Dshell versus INNUENDO Kyle Creyts (Feb 06)
- Re: Dshell versus INNUENDO Dean Pierce (Feb 05)